Subcontracting is a growing trend among companies with skill shortages and hard-to-fill vacancies. In fact, 66 percent of U.S. companies with more than 50 employees outsource certain aspects of their business.
But the more links there are in your supply chain and the more parties involved, the more security risks your company may be exposed to. That’s why, for companies that leverage subcontractors, an effective supply chain risk management strategy is essential to mitigating vulnerabilities and ensuring business continuity.
We recently touched on the importance of supplier risk management in the first installment of our 3-part Risk Management blog series. In this second article, we’ll focus on subcontractors in your digital supply chain—such as developers and technology service partners—and how to manage the security risks they pose.
How Does Supplier Risk Management Work?
Managing supplier risk involves identifying prospective threats, assessing their likelihood of occurrence and potential impact, and devising strategies to minimize damages should these events occur. Part of this strategy involves accepting that risks will always exist among subcontractors. However, you can—and should—prepare for how they could impact your business. When selecting a subcontractor, for example, you’ll want to ensure the company has an adequate risk management program.
Why Is Supplier Risk Management Important?
Subcontractors are essential to many companies’ digital supply chains as they possess advanced technological capabilities that are difficult to replicate internally. But even the most qualified subcontractors come with added risk. And we’re not just talking about budget overruns and late deliveries.
Your business is responsible if a subcontractor breaches or compromises customer or member information. And when hackers attack institutions or big companies, they often target weak links, most notably subcontractors. Retail giant Target is just one of many companies that have faced this issue—they had to pay $18.5 million when a third-party data breach affected 41 million consumers.
To effectively manage the risks in your supply chain, you first need to understand the difference between compliance and security—and how the two are interconnected.
Security vs. Compliance: What’s the Difference?
Third-party requirements, such as industry regulations and government policies, are the primary drivers for compliance. The goal is to establish and improve standards for goods and services throughout the commerce sector. Among the most common compliance programs are GDPR, PCI, HIPAA, and SOX. Your industry and location determine what regulations apply to your company.
Keeping up with these regulations requires consistent reporting and maintenance. Your organization may use internal and third-party resources to align internal controls with compliance program expectations. A supplier failing to follow these regulations can harm your reputation and your bottom line.
A vital part of keeping your company’s integrity intact is monitoring the legal compliance of your partners and subcontractors. At Aquiva, for example, we don’t host or process data, but we support our customers’ auditing and compliance processes, provide supportive policies, and complete questionnaires if required.
Compliance departments often need to consider the operations and controls of subcontractors as part of their audit processes. Obtaining third-party validation of “in scope” suppliers’ controls can reduce audit time and expense. You can use SOC2 and ISO27001 as control frameworks to verify the reliability of your suppliers, especially if they host or process your data.
However, ensuring your contractors are legally compliant doesn’t guarantee your company’s security. In other words, while compliance is an essential component of any risk management program—compliance doesn’t always achieve security.
Cybersecurity realities evolve much faster than compliance frameworks. For reference, GDPR’s latest version is the Data Protection Act 2018, while HIPAA’s dates back to 2013. Therefore, staying compliant isn’t necessarily enough to keep your infrastructure secure—even if compliance frameworks include a review of essential security controls and you run regular tests.
Security involves putting in place a set of technical tools, systems, and processes to protect, defend, and preserve your network, devices, and users. It’s something an organization actively works on to combat unpredictable threats to its assets. There are also no third-party standards to work toward—it needs ongoing maintenance and improvement.
Besides complying with regulations, a robust security program is crucial to strengthening an organization’s security posture and protecting its customers. Aquiva uses CyberGRX to assess our security measures and reinforce our programs with third-party tools.
On top of this, we perform regular checkups: internal security monthly; third parties quarterly; and policies and processes annually. This meticulous approach keeps our management team aware of and focused on security-related matters.
Compliance and security are important components of a supply chain risk management program, and they are both needed to maintain data security. Keeping data safe and protecting your company’s bottom requires aligning corporate compliance with internal security frameworks.
What Is the Ideal Security Framework For Your Business?
Various security frameworks exist, each with their own merits. While industry and geographical factors determine the compliance regulations you must adhere to, choosing a security framework is at your discretion.
So, how do you choose the right framework for your business?
At Aquiva, we’ve adopted and highly recommend the NIST Cybersecurity Framework. Although Aquiva doesn’t leverage subcontractors to support our clients, this framework will allow you to screen service providers and prepare for their inherent security risks. It helps you improve cybersecurity by focusing on the following five functional areas:
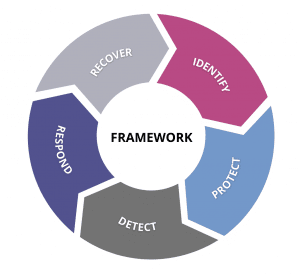
1. Identify
The activities in the Identify function allow you to understand your organization’s vulnerabilities, security posture, and how they relate to corporate risk. Identification is as much about understanding business context as it is a matter of inventory control.
2. Protect
By reducing the effects of threat actor behavior, hardening your assets, managing your policies, and monitoring your workloads, the Protect function allows you to proactively mitigate the impact of a potential cybersecurity threat.
3. Detect
“Assume the breach” has become a mantra among security teams. The Detect function enables the timely discovery of cybersecurity events by ensuring you have the right people, processes, and technology to respond to security events as they occur.
For other, less significant risks, you have a range of options. You may take steps to partially remove a risk, accept it, transfer it, or avoid it altogether.
4. Respond
The Respond function requires organizations to proactively develop a plan to mitigate the impact of a potential cybersecurity incident. An Incident Response Plan is essential—and so is testing this plan periodically. A security event requires clear roles and responsibilities, as well as a clear timeline and communication expectations from leadership.
5. Recover
Each breach will be different, so your recovery process will vary. But at a high level, the Recover function supports the timely recovery to normal operations, ultimately reducing the impact of a security incident. It includes removing threat actors from the overall system, keeping stakeholders informed, and mitigating reputational damage.
During the testing of their controls and as their systems evolve, we advise organizations to incorporate lessons learned and iterative updates across these five functional areas.
We also recommend NIST IR 8374 as both a practical starting point and a validation mechanism for mature security programs. It was developed in partnership with the U.S. Department of Commerce to help businesses prepare for ransomware attacks, an increasingly common threat. It assesses an organization’s readiness to protect itself from ransomware and helps it deal with the consequences of a breach. Moreover, the framework enhances an organization’s overall security posture.
A Practical Approach to Supply Chain Risk Management
Managing supply chain risks associated with subcontractors can be challenging but it shouldn’t feel like an uphill struggle. By using this proven security framework to vet development and other technology services partners you subcontract to, your organization can proactively address and defend against potential cyber risks in your digital supply chain.
Is your security risk management strategy ready for an upgrade?
Next in our series on Security Risk Management, we’ll explore how to conduct security risk assessments for your platform-based partners.
Are you ready to take the first step toward safeguarding your business? Contact us today for more information about our security risk management assessment framework, or to find out how you can develop and implement your own.




